Burp Suite Certified Practitioner (BSCP) Journey #00

Prefaces⌗
Hello. encrypt0r here! I’m about to crack open my experience with the Burp Suite Certified Practitioner (BSCP) exam. This was my first “Practical” cert, a total game-changer after all the theory behind my CASE, and CAP certs.
Thinking of grabbing the BSCP yourself? Buckle up, because this post can be your ultimate guide! We’ll break down the journey, the challenges, and how to land that sweet certification. Big thanks to the teams at Seclab Indonesia for the endless support, and shoutout to everyone on the references listed below – you guys rock!
Hands on the Exam Preparation for the first time⌗
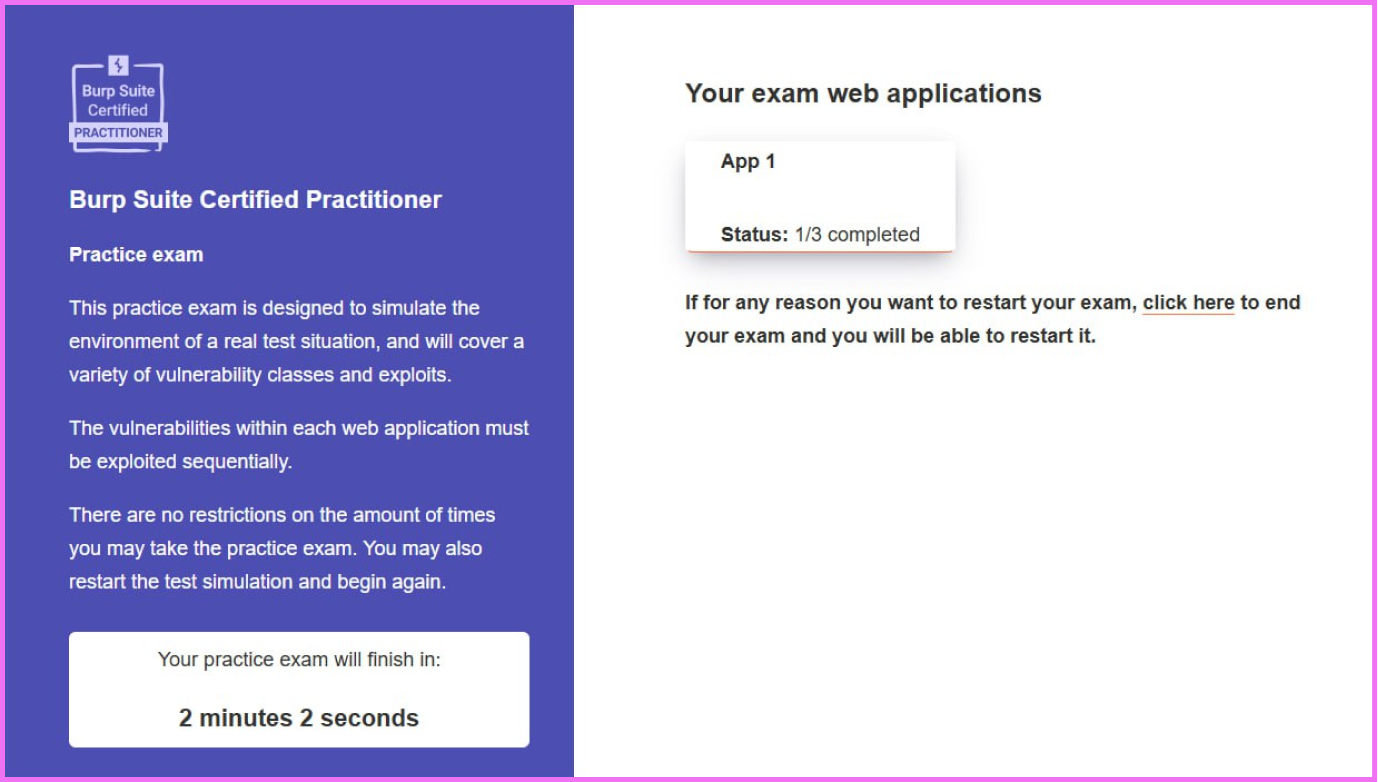
My first attempt at the BSCP exam prep wasn’t exactly smooth sailing. While I hadn’t completed the free labs offered by PortSwigger, I technically didn’t fail. However, I only managed to complete 1 out of the 3 tasks. Turns out, skipping those PortSwigger labs might not have been the best idea!
This exam prep throws three challenges:
- Snag any low-level user account.
- Level up your access to the administrator account.
- Snatch the secret file at /home/user/secret.
You get two hours to conquer these hurdles. In my first attempt, I barely scraped through the first step – grabbing a low-privilege user account. Now, the good news is, I did identify a vulnerability that could escalate my privileges. But overall, it wasn’t exactly a stellar performance (think 1 out of 3, with a healthy dose of “whoops”).
Now, let’s dissect what went wrong. They presented me with a web application featuring a blog search function. Naturally, my focus laser-beamed onto the search bar input, convinced it was an SQL injection waiting to happen. Turns out, I was chasing shadows for a good half hour. Finally, I shifted gears and spent the next hour hunting for XSS vulnerabilities. Here’s where things got interesting: I realized the input was transmitted using JSON. However, to exploit an XSS vulnerability, I needed to understand the JSON object structure first.
Luckily, after some digging, I found an XSS vulnerability and crafted a payload that needed to be sent to the client-side. To make this XSS vulnerability can be exploited, The lab provided an exploit server that mimicked a client, allowing my XSS exploit to take effect. So, I sent a piece of JavaScript that redirected to an endpoint containing my crafted XSS payload as a GET parameter. Then, I waited for my burp collaborator to capture the client session. That’s how I finally gained access to a low-privileged user account – carlos. Phew!
With access to a low-privilege user account, the web application revealed a new feature: Advanced Search. This function allowed users to search blogs using various filtering parameters. With 30 minutes left on the clock, I decided to try my luck with a malicious PostgreSQL Time-Based Blind SQL injection payload in the SortBy parameter. And guess what? It worked! I identified a Time-Based SQL injection vulnerability. However, since I hadn’t prepared any tools to automate an exploit, I ended up chasing after the administrator password until time ran out. Ugh, what a time crunch!
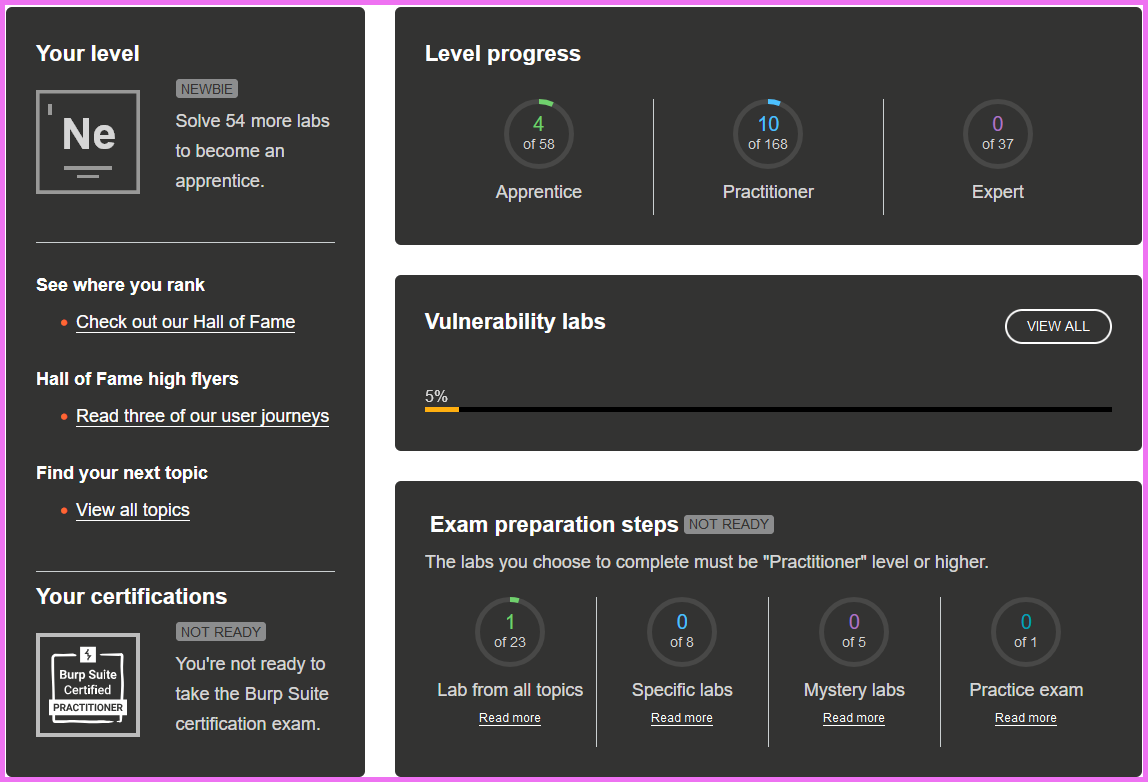
That’s it for today! I’ll be back with another BSCP challenge soon, so keep an eye on the BSCP Series. We’ve still got a long way to go!